Penetration testing, or “pen testing” as it’s often called, is a vital practice in today’s cybersecurity landscape. It involves simulating cyberattacks on your own systems to uncover vulnerabilities before malicious hackers can exploit them. For businesses and organizations, penetration testing plays a critical role in assessing the security of networks, applications, and systems.
Penetration testing is a simulated attack designed to identify vulnerabilities in systems, applications, and networks. It’s performed by ethical hackers who attempt to break into systems just like real attackers would. The goal is not to cause harm but to find weaknesses in security defenses and address them before malicious hackers can exploit them.
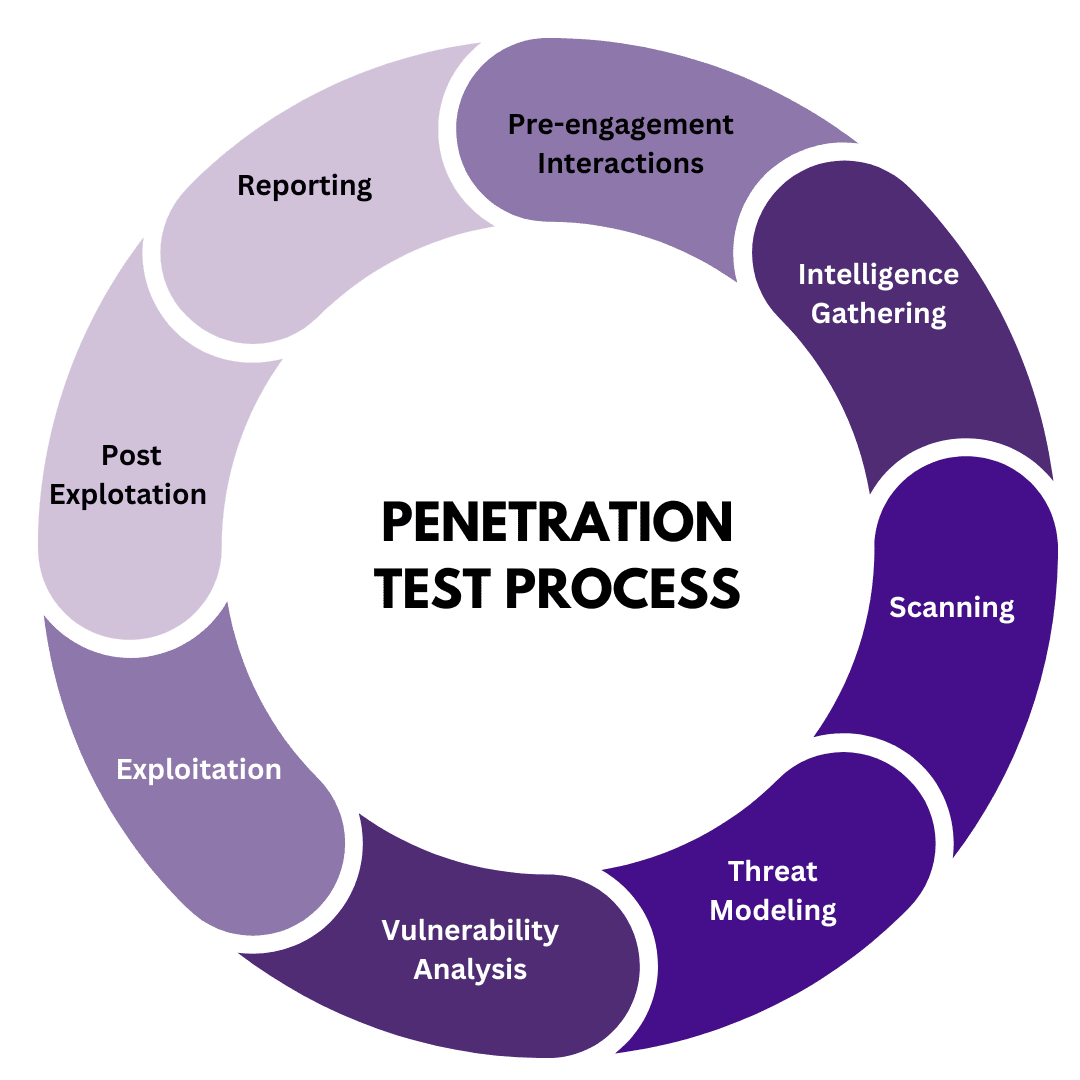
The pen test process generally follows these phases:
- Reconnaissance: Gathering as much information as possible about the target system.
- Exploitation: Using the information gathered to attempt attacks on the system.
- Post-exploitation: Once inside the system, ethical hackers try to gain further access and understand how deep the vulnerabilities go.
- Reporting: Documenting the findings and providing actionable recommendations to fix the identified vulnerabilities.
Penetration tests are essential for a variety of reasons:
- Identify vulnerabilities: Testers can find flaws in security measures like firewalls, encryption, or access controls.
- Compliance: Pen tests help organizations meet regulatory requirements (such as PCI DSS, HIPAA, etc.).
- Improve security posture: Penetration testing is a proactive way to stay ahead of hackers by constantly improving defense mechanisms.
- Real-world simulations: It provides a realistic view of how attackers may infiltrate and exploit systems.
Why Is Penetration Testing Important for Security?
With the rise of cyber threats, it’s no longer enough to rely solely on firewalls, antivirus software, and other basic security measures. Cybercriminals are constantly evolving, employing sophisticated techniques to breach even the most fortified systems. Penetration testing simulates these advanced attacks to proactively identify weaknesses.
Some real-world examples of why penetration testing is crucial:
- Equifax Data Breach (2017): One of the largest data breaches in history, exposing sensitive information of 147 million people. The breach was caused by an unpatched vulnerability in an open-source web application framework, which could have been detected by penetration testing.
- WannaCry Ransomware Attack (2017): A ransomware attack that spread across the globe, targeting Windows systems with a vulnerability in Microsoft’s SMB protocol. Had businesses conducted regular penetration tests, this vulnerability could have been patched before the attack spread.
Penetration testing offers the following key benefits:
- Risk Mitigation: It helps organizations address vulnerabilities before they’re exploited by real attackers.
- Improved Incident Response: Regular pen tests help companies prepare better for potential breaches by identifying gaps in security policies and response plans.
- Boosts Customer Trust: Customers are more likely to trust businesses that proactively take steps to secure their data.
Now that we’ve covered the basics of penetration testing and its importance, let’s dive into the three main types of penetration testing.
The Three Types of Penetration Testing
Overview of the Three Types of Penetration Testing
Penetration testing is not a one-size-fits-all solution. Different types of tests are used based on the level of knowledge the tester has about the system they’re testing. These types are categorized as black box, white box, and gray box. Let’s explore each type in more detail.
1. Black Box Penetration Testing
What is Black Box Penetration Testing?
Black box penetration testing is perhaps the most common type of pen test. In a black box test, the ethical hacker has zero knowledge of the system being tested. They are essentially acting as a “real-world hacker” who has no access to any internal details, network configurations, or source code of the target system.
Black box testers often rely solely on publicly available information about the system (e.g., websites, DNS records, or IP addresses) to gather intelligence, and then attempt to exploit vulnerabilities based on that information.
Advantages of Black Box Penetration Testing
- Simulates Real-World Attacks: Since the tester doesn’t have any internal information, the test mimics how an external attacker would approach your system.
- Focuses on External Security: It’s particularly useful for testing external-facing applications (websites, APIs, etc.) and the network perimeter to assess how vulnerable these points are to hackers.
- Unbiased Perspective: Since the tester has no inside knowledge, they may uncover vulnerabilities that internal team members might miss because they assume certain protections are already in place.
When Should You Use Black Box Penetration Testing?
Black box penetration testing is ideal for:
- Testing publicly accessible systems: If your organization has a website, online application, or external network that can be accessed by anyone on the internet, black box testing can help you find vulnerabilities that a malicious outsider might exploit.
- Simulating external hacker attacks: If you want to assess the effectiveness of your defenses against external attackers, black box testing is your best bet.
Challenges of Black Box Penetration Testing
- Time-Consuming: The tester has no internal knowledge, so they must spend a lot of time on reconnaissance and intelligence gathering before even starting the attack phase.
- Missed Internal Vulnerabilities: Since the tester is looking at the system from an outsider’s perspective, they may miss vulnerabilities that exist within the internal network or those that require insider knowledge.
2. White Box Penetration Testing
What is White Box Penetration Testing?
White box penetration testing, also known as clear-box testing, is quite the opposite of black box testing. In this type of pen test, the tester is provided with full knowledge of the system, including the internal network architecture, source code, configuration details, and access credentials. Essentially, the ethical hacker acts like a security expert within the organization.
This allows for a much more thorough assessment of the system’s security.
Advantages of White Box Penetration Testing
- Comprehensive Testing: Testers can conduct more in-depth tests, identifying vulnerabilities such as code flaws, misconfigurations, or logic errors that may be hard to detect with limited knowledge.
- Faster Testing: Because testers are already familiar with the system, they can bypass the reconnaissance phase and jump straight into the exploitation phase.
- Great for Code Reviews: White box testing is particularly useful for reviewing the source code of custom-built applications for security flaws, such as SQL injection vulnerabilities, insecure authentication, and other weaknesses.
When Should You Use White Box Penetration Testing?
White box penetration testing is ideal for:
- Internal systems testing: If you need to test an internal application or network, white box testing can help uncover weaknesses that would be difficult to spot from the outside.
- Compliance requirements: If your organization is subject to security standards like PCI DSS or HIPAA, white box testing is often required to verify compliance.
- Code audits: For companies that develop their own software, white box testing is an excellent way to conduct security code reviews and ensure no vulnerabilities are built into the system.
Challenges of White Box Penetration Testing
- Potential Bias: Since testers have inside knowledge, they may overlook certain vulnerabilities that an external attacker could exploit. There’s also the risk of being too familiar with the system and missing flaws.
- Time-Consuming and Expensive: Given the extensive knowledge and access required, white box testing is often more expensive and time-consuming than black box testing.
3. Gray Box Penetration Testing
What is Gray Box Penetration Testing?
Gray box penetration testing is a hybrid approach that sits between black box and white box testing. In this type of test, the ethical hacker is given partial knowledge of the system. For example, they may have access to a system’s architecture or internal credentials but not the full source code or detailed network configurations.
The goal of gray box testing is to simulate a scenario where an attacker has gained limited access to a system—perhaps through a phishing attack or by exploiting an insider’s credentials—but does not have complete internal knowledge.
Advantages of Gray Box Penetration Testing
- Balanced Approach: Gray box testing provides a more realistic scenario than black box testing, where attackers might gain some level of internal access, but not full control.
- Efficient and Effective: Because testers are given partial knowledge, they can focus on areas of the system that are most likely to contain vulnerabilities, leading to faster testing.
- Good for Insider Threats: Gray box testing is particularly useful for detecting insider threats or security risks posed by users who have limited access to systems but might exploit it for malicious purposes.
When Should You Use Gray Box Penetration Testing?
Gray box testing is ideal for:
- Testing internal applications: For organizations that want to test their internal systems with partial knowledge (such as employee credentials), gray box testing can reveal critical flaws.
- Simulating insider threats: Gray box testing is a great way to mimic attacks where the attacker has gained partial access to the network, whether through phishing, password theft, or another method.
Challenges of Gray Box Penetration Testing
- Limited Realism: While gray box tests simulate real-world attack scenarios, they may not be as thorough as white box testing.
- Hard to Scope: Defining the exact amount of information to be shared with testers can be tricky, making it challenging to keep the test realistic.

How Do You Choose Between the Three Types of Penetration Testing?
How to Select the Right Type of Penetration Testing for Your Organization
Choosing the right type of penetration testing depends largely on the goals of your security program, the systems you’re testing, and your available resources. Here are some key factors to consider when deciding between black box, white box, and gray box penetration testing.
- Security Goals
- If your primary goal is to identify external vulnerabilities (e.g., in your website, application, or network perimeter), black box testing is ideal. This approach simulates an external attacker attempting to breach your system without any insider knowledge.
- If you’re focusing on internal system weaknesses or need to ensure that internal users can’t easily bypass security measures, white box testing is a great choice. This type is also necessary for compliance audits or code reviews.
- If you want to test for insider threats or the security posture of users with limited access to your network, gray box testing is your best option. It’s also useful when you need to test the overall integrity of the system with partial knowledge, such as from an employee who may have gained unauthorized access.
- Budget and Resources
- Black box testing can be more cost-effective because it focuses primarily on external systems and doesn’t require deep access to internal resources. However, because it can be more time-consuming, the costs may add up if you’re testing large-scale or complex systems.
- White box testing generally requires more resources, as testers need to be highly skilled in reviewing source code, configuration files, and internal architecture. This testing type is often more expensive due to the level of access and detail involved.
- Gray box testing offers a middle ground, making it more affordable and efficient than white box testing, but still allowing for significant insights into the system’s internal structure.
- Testing Scope
- Black box tests are best for assessing the outer perimeter of your network, focusing on areas such as websites, firewalls, and any system that an external attacker could access.
- White box tests cover internal security vulnerabilities—from network configurations to source code and application logic—providing a thorough audit of your infrastructure.
- Gray box tests offer a balanced approach, ideal for systems where an insider might exploit their limited access. It’s especially useful for testing scenarios where employees or contractors have some level of access but not full internal knowledge.
Examples of Use Cases for Each Penetration Test Type
To help illustrate when each type of penetration testing is used, consider these examples:
- Black Box Penetration Testing:
- Testing a Website: A company wants to test its website for vulnerabilities. Penetration testers have no internal knowledge and must discover and exploit vulnerabilities based on publicly available information, just like an external hacker.
- External Network Penetration Testing: Testing a company’s external-facing network infrastructure, such as firewalls, routers, and publicly accessible applications.
- White Box Penetration Testing:
- Code Review for a Custom Application: A business has developed a custom web application and needs to ensure that its source code doesn’t contain vulnerabilities such as SQL injection or cross-site scripting (XSS). In this case, testers would have access to the source code to identify issues.
- Compliance Testing: A healthcare organization undergoing HIPAA compliance testing would require a thorough examination of its internal systems and network, with testers using white box techniques to assess security controls against standards.
- Gray Box Penetration Testing:
- Employee Access Testing: An organization wants to simulate an attack from a disgruntled employee who has limited access to the network. Testers would have partial access to internal systems, perhaps an employee’s account credentials, and attempt to escalate their privileges.
- Network Segmentation Testing: Companies that implement strict internal network segmentation can use gray box testing to evaluate if an attacker with limited access could navigate across network boundaries and access restricted data.
Benefits and Limitations of Each Penetration Testing Type
Comparing the Pros and Cons of Each Type of Penetration Testing
Each type of penetration test has its strengths and weaknesses. Below, we’ll compare black box, white box, and gray box tests based on key factors such as depth of testing, realism, cost-effectiveness, and speed.
| Factor | Black Box Penetration Testing | White Box Penetration Testing | Gray Box Penetration Testing |
|---|---|---|---|
| Realism | Highly realistic for external attacks. | Not as realistic for external threats. | Good balance, simulates insider threats. |
| Depth of Testing | Limited depth (focuses on external systems). | Comprehensive, deep testing of systems, networks, and code. | Moderate depth, testing internal and external access. |
| Time Required | Longer, due to reconnaissance phase. | Faster (no need for external intelligence gathering). | Faster than white box testing but more detailed than black box. |
| Cost | Generally lower cost. | Higher cost due to in-depth testing. | Middle ground cost. |
| Vulnerabilities Found | Limited to external vulnerabilities. | Uncovers a wide range of vulnerabilities, including hidden internal flaws. | Identifies internal vulnerabilities that are exploitable from external access. |
| Scope of Testing | External-facing systems, networks. | Internal systems, source code, configuration files. | Internal systems and limited knowledge of the infrastructure. |
Pros of Black Box Testing:
- Realistic external attack simulation.
- Unbiased approach, as testers see the system without prior knowledge.
- Uncovers vulnerabilities that external attackers might exploit.
Cons of Black Box Testing:
- Takes more time due to the need for initial information gathering.
- Might miss vulnerabilities that require deeper internal access.
Pros of White Box Testing:
- Provides a thorough and comprehensive assessment.
- Can uncover hidden vulnerabilities (like logic flaws) and internal security weaknesses.
- Ideal for security audits and ensuring compliance.
Cons of White Box Testing:
- Requires more resources and higher costs.
- Testers may overlook obvious vulnerabilities because they are too familiar with the system.
Pros of Gray Box Testing:
- Offers a balanced approach.
- Good for testing real-world scenarios, such as an attacker who gains partial access to a network.
- Faster than white box testing while still covering significant internal vulnerabilities.
Cons of Gray Box Testing:
- Limited testing scope compared to white box.
- Harder to scope and define the level of knowledge testers should have.
Penetration Testing Best Practices
Penetration Testing Best Practices to Follow
When conducting any type of penetration testing, it’s important to follow best practices to ensure the test is effective, secure, and provides actionable insights. Here are some best practices to keep in mind:
- Define the Scope Clearly: Before starting any penetration test, ensure that both the testers and the organization agree on the scope of the test. This includes specifying which systems are in-scope and which are out-of-scope, ensuring there are no legal or ethical issues.
- Use Qualified Professionals: Ensure that penetration testers have the necessary skills and certifications, such as Certified Ethical Hacker (CEH) or Offensive Security Certified Professional (OSCP).
- Create a Communication Plan: Plan how vulnerabilities will be reported and communicated. It’s important to ensure that there is a clear and safe channel for testers to report findings without causing any panic or disruption.
- Retest After Fixes: Once vulnerabilities are fixed, conduct retests to ensure that the fixes work and that no new vulnerabilities have been introduced.
Common Pitfalls to Avoid in Penetration Testing
- Skipping Scope Definition: Not setting clear boundaries for the test can result in unintentional disruptions, legal issues, or missed vulnerabilities.
- Ignoring Post-Test Actions: After testing, it’s crucial to address the vulnerabilities found. Ignoring this step can leave your systems exposed to potential exploits.
- Overlooking Social Engineering: Many external attacks begin with social engineering tactics. Ensure that social engineering is part of your penetration testing, especially in black box tests.
Penetration Testing Tools and Techniques
Popular Penetration Testing Tools
While penetration testing relies heavily on the expertise of the testers, a number of specialized tools are often used to facilitate the testing process. These tools are tailored to different types of tests, helping professionals identify vulnerabilities, simulate attacks, and assess the overall security posture of systems. Below, we’ll explore some popular penetration testing tools commonly used across black box, white box, and gray box testing:
- Kali Linux
Kali Linux is a powerful and widely used penetration testing distribution that comes with numerous tools for vulnerability assessment, exploitation, and reporting. Kali is often used for black box testing because it contains tools like Nmap (for network scanning) and Wireshark (for packet sniffing) that are great for external reconnaissance and exploitation. - Metasploit Framework
Metasploit is one of the most widely known tools for exploiting vulnerabilities and conducting attacks. It is suitable for all types of penetration tests, especially black box testing, as it helps simulate sophisticated exploits. Testers use Metasploit to gain access to systems, escalate privileges, and exploit known vulnerabilities. - Burp Suite
Burp Suite is an essential tool for web application testing, particularly for black box penetration testing. It allows security testers to perform various functions like web crawling, vulnerability scanning, and man-in-the-middle attacks. The Pro version is especially useful for automated scanning of web vulnerabilities such as SQL injection and cross-site scripting. - Nmap
Nmap is another tool used predominantly in black box testing for discovering devices and services running on a network. It helps identify vulnerabilities in the network infrastructure by scanning open ports, services, and their corresponding vulnerabilities. - OWASP ZAP (Zed Attack Proxy)
This is a tool used for web application security testing and is particularly effective in white box and gray box testing. ZAP is an open-source tool that helps penetration testers find vulnerabilities in web applications, including input validation issues, authentication flaws, and authorization weaknesses. - Nikto
Nikto is a web server scanner that can be used during black box testing to discover vulnerabilities in web servers, such as outdated software versions or misconfigurations. Nikto can detect a wide range of potential issues and help identify weak points in your web-facing infrastructure. - John the Ripper
A popular tool for brute force password cracking, John the Ripper is typically used in gray box testing to simulate attacks from users with some internal access. It helps security testers identify weak passwords or easily guessable passwords that could allow an attacker to escalate privileges.
Techniques Employed in Penetration Testing
Penetration testing employs various techniques, which depend on the type of test being conducted and the specific vulnerabilities the tester is trying to exploit. Here are some of the most common techniques used:
- Social Engineering
- Description: Social engineering attacks exploit human behavior, rather than relying on technical vulnerabilities, to gain unauthorized access. This is often part of black box and gray box testing, where the tester may attempt to manipulate employees into disclosing confidential information (e.g., passwords, access codes).
- Example: Phishing, pretexting (pretending to be someone else), or baiting (leaving malicious USB drives in public spaces).
- Vulnerability Scanning
- Description: Vulnerability scanning involves using automated tools to scan systems for known weaknesses, such as unpatched software, misconfigurations, or weak encryption algorithms. This technique is often part of white box testing when testers have access to the system’s architecture and source code.
- Example: Scanning for outdated versions of software using tools like OpenVAS or Nessus.
- Brute Force Attacks
- Description: A brute force attack involves systematically trying all possible passwords or encryption keys until the correct one is found. This is a common technique used in gray box testing to test password strength and authentication protocols.
- Example: Cracking weak passwords using tools like Hydra or John the Ripper.
- SQL Injection
- Description: SQL injection occurs when attackers inject malicious SQL queries into a web application to manipulate the database. This technique is commonly tested for during white box testing to identify flaws in input validation and data handling.
- Example: Inserting
OR 1=1into input fields like login forms to bypass authentication.
- Privilege Escalation
- Description: Privilege escalation involves gaining higher levels of access once an attacker has compromised a system. In gray box and white box testing, this technique is used to identify weaknesses in user permissions and access control mechanisms.
- Example: A tester might try to escalate from a low-privileged user account to administrative privileges on a Windows or Linux system.
- Network Sniffing and Man-in-the-Middle Attacks
- Description: Sniffing involves intercepting and analyzing network traffic to capture sensitive data, such as passwords or credit card information. This technique is often used in black box testing to simulate an attacker intercepting traffic between the user and the server.
- Example: Using Wireshark to capture unencrypted communications and extract sensitive information.
- Exploiting Known Vulnerabilities
- Description: Penetration testers often leverage known vulnerabilities in widely used software (such as operating systems, applications, or network devices) to gain access to a system. This is a technique used in all types of penetration testing, though it’s particularly effective in black box testing.
- Example: Exploiting a vulnerability in a Windows SMB protocol or a Drupal vulnerability to gain unauthorized access.
Choosing the Right Tools and Techniques for Each Test Type
- Black Box Testing: Tools like Nmap, Metasploit, and Burp Suite are key in discovering external vulnerabilities and attempting to exploit them. Techniques like social engineering, vulnerability scanning, and network sniffing are often used.
- White Box Testing: Tools like OWASP ZAP, Nikto, and Burp Suite (with more focus on code and system-level vulnerabilities) are suitable for white box testing. Techniques such as source code review, vulnerability scanning, and SQL injection are common.
- Gray Box Testing: Testers can use a mix of black box and white box tools. Techniques like privilege escalation, brute force attacks, and social engineering work well for testing both internal and external system vulnerabilities.
Common Pitfalls to Avoid in Penetration Testing
While penetration testing is an essential cybersecurity tool, there are several common mistakes and pitfalls that organizations should avoid to ensure the testing process is effective and delivers actionable results. Whether you’re conducting a black box, white box, or gray box test, here are some of the most frequent errors to watch out for:
1. Failing to Define the Scope Properly
One of the most critical aspects of any penetration test is a well-defined scope. The scope outlines which systems, networks, and applications will be tested, and which ones will be off-limits. Without a clear scope, testers might accidentally disrupt important systems, cause downtime, or miss critical areas of the network that need testing.
- Solution: Ensure that both parties—the client (organization) and the penetration testing team—have a clear understanding of the boundaries. This includes setting up rules for what can and cannot be tested (e.g., systems outside of the organization’s perimeter, third-party services, etc.).
2. Not Performing Regular Tests
Many organizations think of penetration testing as a one-time event, often only after a breach has occurred or during a major security overhaul. However, this approach can leave systems vulnerable to evolving threats.
- Solution: Penetration tests should be conducted regularly—ideally, on an annual basis or after significant changes to your infrastructure (such as network updates, new software deployments, or when rolling out new applications). Frequent testing helps identify new vulnerabilities and ensures that existing defenses remain effective.
3. Underestimating the Need for Post-Test Action
A penetration test can uncover numerous vulnerabilities, but the findings are only valuable if organizations take action. Often, after a test, companies fail to implement the necessary fixes, leaving vulnerabilities unaddressed.
- Solution: After receiving the test report, prioritize vulnerabilities based on their risk level and potential impact. Implement patches, configuration changes, and security measures to address the identified issues. It’s also a good practice to conduct retests to ensure that fixes have been successfully applied and no new vulnerabilities have been introduced.
4. Ignoring Social Engineering Attacks
Social engineering is often one of the most effective attack techniques used by malicious hackers. Penetration testing should never solely focus on technical vulnerabilities; it should also test how well your employees are trained to recognize and respond to phishing emails, pretexting, and other social engineering tactics.
- Solution: Incorporate social engineering scenarios into your penetration testing. Test whether employees are susceptible to phishing attacks, whether they follow security protocols, and whether they know how to spot suspicious activity. This will help you address human vulnerabilities in addition to technical ones.
5. Using Inexperienced or Unqualified Penetration Testers
Penetration testing requires a high level of expertise, especially when dealing with complex systems, code reviews, and security audits. Using inexperienced testers can lead to incomplete assessments or missed vulnerabilities.
- Solution: Ensure that the penetration testing team has the right certifications (e.g., Certified Ethical Hacker (CEH), Offensive Security Certified Professional (OSCP)), experience with your industry, and an in-depth understanding of the types of tests being performed (black, white, gray). Choose professionals with a strong track record in ethical hacking and security assessments.
6. Failing to Test the Entire Attack Surface
Some organizations make the mistake of focusing solely on certain systems (like their public website or the main internal network) while ignoring other parts of their infrastructure that could also be vulnerable, such as third-party services, employee endpoints, or cloud infrastructure.
- Solution: Penetration tests should cover the entire attack surface of your network. This includes web applications, cloud environments, remote work setups, endpoints (e.g., laptops and mobile devices), and third-party services that might have access to your network. A comprehensive test will give you a much clearer picture of your organization’s overall security.
7. Overlooking the Importance of Reporting and Communication
A penetration test is only as useful as the quality of its final report. Simply identifying vulnerabilities isn’t enough; the reporting phase of a penetration test should provide clear, actionable recommendations for addressing the issues found.
- Solution: Ensure that the test results are clearly documented, with easy-to-understand explanations of the vulnerabilities, their potential risks, and step-by-step remediation guidance. The report should be targeted to the technical team (for remediation purposes) and management (for decision-making and resource allocation).
Penetration Testing Myths Debunked
Despite the clear benefits of penetration testing, several myths persist that can hinder organizations from fully embracing this important security practice. Here, we’ll debunk some of the most common myths:
Myth 1: Penetration Testing is Only for Large Enterprises
Penetration testing is often associated with large organizations that have complex systems and high-value targets. However, small and medium-sized businesses (SMBs) are just as vulnerable to cyberattacks—if not more so, as they are often targeted by cybercriminals due to their perceived weaker defenses.
- Reality: Penetration testing is important for organizations of all sizes. Whether you’re a startup or a multinational corporation, testing your systems for vulnerabilities will help identify potential weak spots and mitigate the risk of a breach.
Myth 2: Penetration Testing is Only About Finding Bugs
While penetration testing does indeed involve finding vulnerabilities, it is also about assessing the overall security posture of an organization. Pen testers evaluate how well an organization’s security defenses hold up against simulated attacks and assess the effectiveness of access controls, encryption, and other security measures.
- Reality: Penetration testing is about simulating real-world attacks to assess how well your organization’s security measures stand up to an adversary’s efforts. It’s about more than just finding bugs; it’s about testing the resilience of your entire security ecosystem.
Myth 3: Once You Conduct Pen Testing, You’re Secure
Many organizations believe that a single penetration test will solve all their cybersecurity problems. In reality, security is a continuous process that requires regular updates, ongoing monitoring, and retesting.
- Reality: Penetration testing is an ongoing process. Threats evolve constantly, and new vulnerabilities are discovered every day. To stay secure, organizations must conduct regular tests, patch vulnerabilities, and continuously strengthen their defenses against emerging threats.
Strengthening Your Security with the Right Penetration Test
Penetration testing is a cornerstone of any effective cybersecurity strategy. By understanding the three types of penetration tests—black box, white box, and gray box—organizations can tailor their testing efforts to their specific security goals. Whether you’re simulating an external attack, performing an in-depth code review, or testing for insider threats, penetration testing provides valuable insights that can help you bolster your defenses and reduce the risk of a successful cyberattack.
By following best practices, addressing common pitfalls, and leveraging the right tools, organizations can maximize the effectiveness of penetration tests and stay ahead of evolving cyber threats.
If you’re ready to take your security to the next level, it’s time to engage in comprehensive and targeted penetration testing. Reach out to a trusted cybersecurity provider today to help safeguard your systems and data from potential vulnerabilities.