Penetration testing, often called pen testing, is a critical process in cybersecurity that involves simulating cyberattacks to evaluate the security of an organization’s systems. These tests are designed to uncover vulnerabilities before malicious actors can exploit them. By identifying weaknesses, organizations can patch them, fortify defenses, and improve their overall security posture.
Purpose of Penetration Testing
The primary goal of penetration testing is to identify vulnerabilities and assess how well a system can withstand cyber threats. Think of it as hiring ethical hackers to proactively test your system’s defenses.
Some common objectives include:
- Discovering security loopholes in networks, applications, or physical systems.
- Validating the effectiveness of existing security controls.
- Assessing an organization’s compliance with industry regulations (e.g., PCI DSS, HIPAA).
- Strengthening customer and stakeholder trust by demonstrating proactive security measures.
Types of Penetration Testing
There are several categories of penetration testing, each targeting specific areas of an organization’s security:
- Network Penetration Testing:
Focuses on discovering vulnerabilities in wired and wireless networks, including firewalls, routers, and servers. - Web Application Penetration Testing:
Targets vulnerabilities in web applications, such as SQL injection, cross-site scripting (XSS), and session hijacking. - Social Engineering Penetration Testing:
Simulates attacks that exploit human psychology, such as phishing, pretexting, or baiting. - Physical Penetration Testing:
Tests the security of physical premises, such as locks, biometric systems, and surveillance cameras.
Skills Needed for Penetration Testing
To excel in penetration testing, a mix of technical and soft skills is necessary.
General Skills
- Critical Thinking: Pen testers must think like attackers to anticipate possible breach scenarios.
- Problem-Solving: Quickly devising solutions for vulnerabilities found during testing.
- Communication Skills: Writing detailed reports for technical and non-technical audiences.
Technical Skills
- Networking Knowledge: Understanding protocols, firewalls, and configurations.
- Operating System Proficiency: Expertise in Linux and Windows environments.
- Familiarity with Tools: Experience with platforms like Metasploit, Nmap, and Burp Suite.
These foundational skills lay the groundwork for effective penetration testing. But one critical question remains: Does penetration testing require coding?

The Role of Coding in Penetration Testing
One of the most common questions aspiring cybersecurity professionals ask is whether penetration testing requires coding skills. The short answer is: coding is not strictly necessary but is highly advantageous. While tools and frameworks can accomplish many tasks, knowing how to code unlocks more opportunities for customization, efficiency, and creativity during a penetration test.
Is Coding Essential for Penetration Testing?
For many entry-level penetration testing roles, coding is not an absolute requirement. Prebuilt tools such as Nmap, Metasploit, and Burp Suite handle a wide variety of tasks, from vulnerability scanning to exploiting known weaknesses. These tools come with user-friendly interfaces or pre-written scripts that allow users to conduct tests without writing code.
However, as you advance in your career, coding becomes increasingly valuable. Many real-world scenarios require solutions tailored to specific environments, which off-the-shelf tools cannot always provide. For example:
- Developing a custom exploit for a previously unknown vulnerability.
- Modifying existing scripts to bypass security measures.
- Automating repetitive tasks to save time.
Thus, while you can begin your career without coding, it’s advisable to learn coding skills if you want to excel as a penetration tester.
Advantages of Knowing How to Code
Understanding programming languages offers significant benefits for penetration testers. Here’s how coding knowledge can enhance your capabilities:
- Customizing Tools and Scripts:
Many tools rely on scripts written in languages like Python, Ruby, or Perl. Knowing how to read and modify these scripts allows you to tailor them for specific scenarios. - Automating Tasks:
Coding enables you to automate repetitive tasks such as scanning large networks or analyzing vast amounts of data, freeing up time for more complex activities. - Understanding Exploits:
To exploit vulnerabilities effectively, you need to understand the underlying code. For example, if a web application has a SQL injection vulnerability, knowledge of how SQL queries work is crucial. - Debugging and Problem Solving:
When tools or scripts fail, coding skills allow you to troubleshoot issues, fix errors, and continue testing without delays.
Penetration Testing Without Coding
It’s entirely possible to contribute to penetration testing efforts without extensive coding knowledge, especially at the beginning of your career. Some scenarios where coding might not be necessary include:
- Using Prebuilt Tools: Tools like Nessus, OpenVAS, and Wireshark provide robust capabilities without requiring custom scripts.
- Manual Testing Techniques: Some vulnerabilities, such as insecure passwords or improper configurations, can be identified without writing code.
- Team Collaboration: Penetration testing often involves teams with diverse skill sets. Non-coders can focus on reconnaissance, report writing, or running prebuilt tools while coders handle customizations.
Coding is not a strict requirement for penetration testing but can significantly expand what you can accomplish. Whether you aim to rely on prebuilt tools or develop your own, understanding the role of coding in pen testing will help you make informed career decisions.
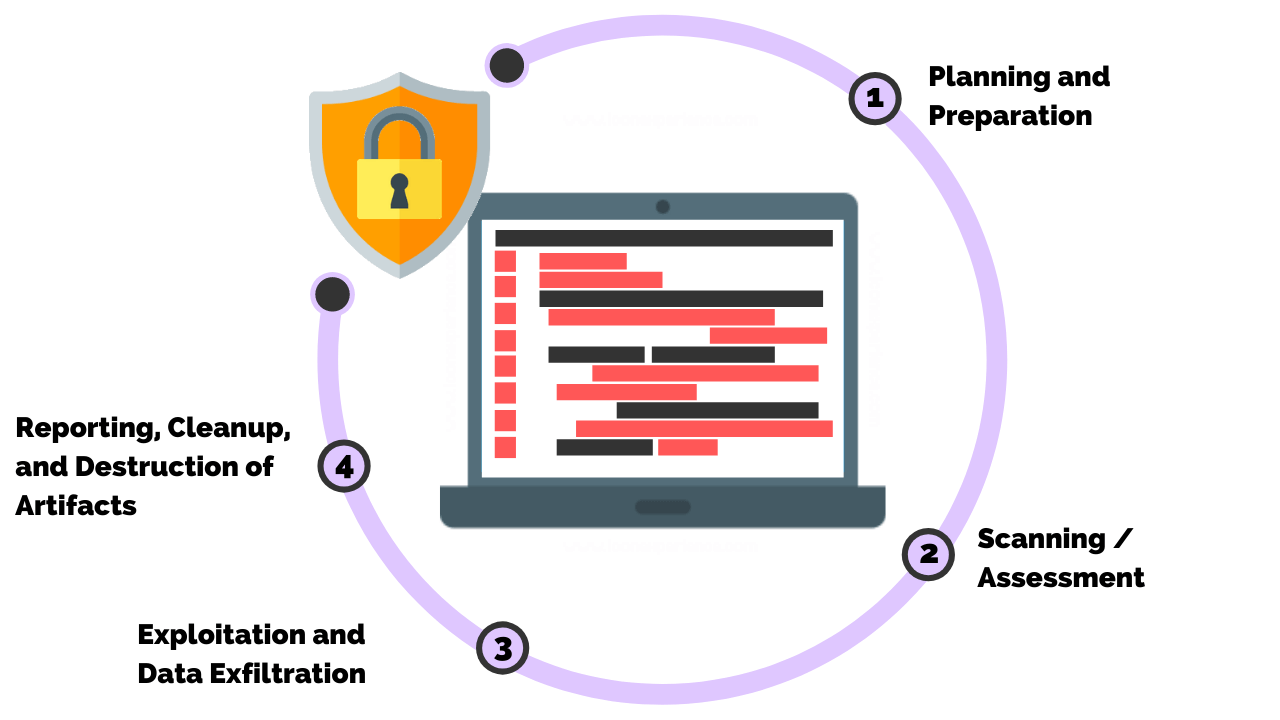
How Much Coding Do You Need to Know?
The amount of coding required for penetration testing depends on your role, the complexity of the environment you’re testing, and your career goals. While beginner-level testers may only need a basic understanding, advanced roles demand a more profound coding skill set. Let’s break it down.
Coding for Beginner vs. Advanced Penetration Testers
For Beginners
As an entry-level penetration tester, you don’t need to master programming immediately. Many tasks can be completed using graphical tools or pre-written scripts. However, having some foundational knowledge will give you a competitive edge.
Beginner-friendly skills to focus on:
- Basic Scripting: Learn how to write and modify simple scripts in Python or Bash.
- Understanding Code Logic: Recognize how loops, conditions, and variables work in scripts.
- Tool Customization: Know how to tweak parameters in tools like Metasploit or Nmap.
For Advanced Testers
Senior penetration testers often encounter scenarios where prebuilt tools fall short. Advanced roles require a deeper understanding of programming to:
- Develop custom exploits.
- Reverse-engineer malware or binaries.
- Test highly specialized systems.
Advanced coding knowledge includes:
- Writing Complex Scripts: Automate sophisticated tasks or create entirely new testing tools.
- Programming Exploits: Understand how to craft exploits for vulnerabilities such as buffer overflows.
- Working with APIs: Use APIs to interact with third-party systems during tests.
Programming Languages for Penetration Testing
Certain programming languages are more relevant to penetration testing due to their functionality and versatility. Below is a list of recommended languages and how they are used:
| Language | Use Case |
|---|---|
| Python | Writing scripts for automation, network scanning, and tool customization. |
| Bash | Automating Linux tasks and managing shell-based scripts. |
| JavaScript | Testing web application vulnerabilities such as XSS and CSRF. |
| C/C++ | Writing low-level exploits and understanding buffer overflows. |
| Assembly | Reverse engineering and exploit development for binary applications. |
| Ruby | Customizing Metasploit scripts and modules. |
Focus Areas for Beginners
- Start with Python due to its simplicity and wide adoption in cybersecurity.
- Learn Bash scripting to navigate and automate tasks in Linux environments.
- Explore JavaScript basics to test common web application vulnerabilities.
Focus Areas for Advanced Professionals
- Dive into C/C++ and Assembly to understand how software vulnerabilities work at a deeper level.
- Practice creating custom Metasploit modules using Ruby.
How to Prioritize Learning?
It’s easy to feel overwhelmed by the number of languages to learn. A practical approach is:
- Start with Python for scripting and automation.
- Learn Bash for command-line efficiency.
- Gradually expand to other languages like C or Assembly as your career progresses.
Real-World Example: The Value of Coding
Consider a scenario where a web application’s login page is vulnerable to SQL injection. While a prebuilt tool might flag the issue, understanding SQL syntax allows you to write custom queries that exploit the vulnerability further. Similarly, during a reverse-engineering task, coding knowledge enables you to dissect and modify malware to understand its behavior.
The depth of coding knowledge required depends on your role and aspirations. Beginners can focus on scripting basics, while advanced testers benefit from mastering multiple languages.
Tools and Techniques That Reduce Coding Needs
While coding is a powerful skill for penetration testers, the field offers a wide range of tools and techniques that can perform complex tasks without requiring significant programming knowledge. These tools help streamline processes, automate common actions, and make penetration testing accessible to those still learning to code.
Prebuilt Penetration Testing Tools
Several powerful tools are designed to handle the heavy lifting in penetration testing, requiring little to no coding skills. Below is an overview of widely used tools and their functionalities:
| Tool | Functionality | Coding Required? |
|---|---|---|
| Metasploit | Exploitation framework for identifying, validating, and exploiting vulnerabilities. | Minimal (scripts optional). |
| Burp Suite | Web application vulnerability scanner and exploitation tool. | No (GUI-driven). |
| Nmap | Network discovery and vulnerability scanning. | No (command-line usage). |
| Wireshark | Network protocol analyzer for capturing and inspecting network traffic. | No. |
| Nessus | Automated vulnerability scanning for networks and systems. | No. |
| Kali Linux | A Linux distribution preloaded with numerous pen testing tools. | No (tool-specific). |
These tools are highly effective for initial testing phases like reconnaissance, scanning, and exploiting known vulnerabilities. For example, Metasploit offers an extensive library of prewritten exploits, and Nessus automatically scans for common vulnerabilities in networks and servers.
Case Study: Using Metasploit Without Coding
A penetration tester using Metasploit might select an exploit module, configure it using a simple interface, and launch the attack. For example:
- Select an exploit targeting a known Windows vulnerability.
- Set parameters like the target IP address.
- Execute the exploit and observe the results.
This process requires no programming, showcasing how prebuilt tools can simplify penetration testing.
Automation Through Scripting
For testers seeking to automate repetitive tasks without diving deep into coding, simple scripts can be a valuable asset. Learning basic scripting concepts can help:
- Automate network scans for specific IP ranges.
- Parse large data files for relevant information.
- Schedule tasks like daily vulnerability scans.
Example: Automating Scans with Python
A beginner-friendly Python script might look like this:
This script uses Python to automate an Nmap scan, demonstrating how basic scripting can save time.
Situations Where Coding Becomes Necessary
While tools minimize the need for programming, there are scenarios where coding skills become indispensable:
- Custom Payloads: Prebuilt tools may not include payloads for every scenario. Creating your own requires coding expertise.
- Script Modification: Tools like Metasploit use languages like Ruby for their modules. Tweaking these modules often requires coding.
- Exploiting Zero-Day Vulnerabilities: New and undocumented vulnerabilities demand a custom approach, often involving coding from scratch.
Example: Writing a Custom Payload
In advanced penetration testing, you might need to craft a payload that bypasses antivirus software. Python is often used for such tasks:
This script creates a simple reverse shell, demonstrating the power of coding in advanced pen testing scenarios.
Balancing Tools and Coding
The key to success as a penetration tester is balancing the use of tools with coding skills. Beginners can rely heavily on prebuilt tools while gradually integrating scripting into their workflow. Advanced testers use a mix of tools and coding to create customized solutions for unique challenges.