Penetration testing is an essential practice in the world of cybersecurity. It is a proactive approach to identifying vulnerabilities in systems, networks, and applications before malicious hackers can exploit them. But how is penetration testing done?
penetration testing is a method used by cybersecurity professionals to simulate cyberattacks on an organization’s systems in order to uncover vulnerabilities that could be exploited by real attackers. Unlike vulnerability scanning, which focuses on identifying known vulnerabilities, penetration testing goes further by exploiting those vulnerabilities to see how far an attacker could go if they gained unauthorized access to the system.
Penetration tests are often referred to as “ethical hacking” because they are performed with the permission of the organization and follow strict ethical guidelines. These tests help identify weak points in an organization’s security infrastructure, including networks, applications, wireless networks, and even human behavior.
Purpose of Penetration Testing
The main goals of penetration testing are:
- Identifying vulnerabilities: Discovering weaknesses before they can be exploited by malicious actors.
- Demonstrating the impact of vulnerabilities: Showing how an attack could compromise the system, steal data, or cause damage.
- Validating security measures: Ensuring that existing security controls and defenses are effective.
- Compliance: Meeting regulatory requirements and industry standards, such as PCI DSS, HIPAA, and GDPR.
In simple terms, penetration testing is an effective way to discover potential attack vectors and take steps to mitigate risks before a real cyberattack occurs.
Types of Penetration Testing
There are several types of penetration testing that focus on different areas of security. Each type serves a specific purpose depending on the scope and target of the test.
1. External Penetration Testing
External penetration testing simulates an attack from an outside source—like a hacker attempting to breach the organization’s systems from the internet. The goal is to identify vulnerabilities in publicly accessible systems such as web servers, email servers, and DNS servers. Testers may attempt to exploit these vulnerabilities to gain unauthorized access to the internal network.
2. Internal Penetration Testing
Internal penetration testing focuses on the internal network. It simulates an attack by a malicious insider or an external hacker who has gained access to the network. Testers explore potential attack vectors from within the system, such as accessing sensitive data or escalating privileges to compromise critical resources.
3. Web Application Penetration Testing
Web applications are common targets for hackers due to their exposure on the internet. Web application penetration testing targets websites, mobile apps, APIs, and other online services. The goal is to identify vulnerabilities such as SQL injection, cross-site scripting (XSS), or authentication flaws.
4. Mobile Application Penetration Testing
With the rise of mobile devices, testing the security of mobile apps has become more important. Mobile application penetration testing focuses on security flaws within mobile applications, ensuring that sensitive data is protected and the app does not contain vulnerabilities that could be exploited by cybercriminals.
5. Wireless Network Penetration Testing
Wireless networks are an essential part of modern infrastructures, but they are also vulnerable to attack. In wireless network penetration testing, testers assess the security of Wi-Fi networks, looking for weak encryption, unauthorized access points, and other vulnerabilities that could allow attackers to gain access to the network.
6. Social Engineering Penetration Testing
While most penetration testing focuses on technical vulnerabilities, social engineering penetration testing aims to exploit human factors. This includes tactics such as phishing, pretexting, or baiting to manipulate employees into divulging sensitive information or allowing unauthorized access.
Benefits of Penetration Testing
Penetration testing is invaluable for any organization concerned about cybersecurity. Some of the key benefits include:
- Proactive identification of vulnerabilities: By identifying weaknesses early, organizations can fix them before they become security incidents.
- Improved defense posture: Penetration tests help improve the overall security infrastructure, making it harder for attackers to succeed.
- Regulatory compliance: Many industries require regular penetration testing to meet compliance standards. This is especially true for sectors like finance, healthcare, and e-commerce.
- Building trust: By conducting penetration tests, organizations can demonstrate to clients, partners, and stakeholders that they take cybersecurity seriously.
The results of a successful penetration test can significantly strengthen an organization’s cybersecurity defenses and reduce the likelihood of a real-world breach.
Common Vulnerabilities Found During Penetration Testing
Penetration tests are typically designed to identify a wide range of vulnerabilities that could be exploited by attackers. Some of the most common vulnerabilities include:
- Outdated software: Unpatched systems and software can provide easy targets for attackers, as many known vulnerabilities have well-documented exploits.
- Weak passwords: Brute force attacks and password spraying can crack weak or reused passwords, giving attackers access to critical systems.
- Misconfigured servers and firewalls: Improper configurations can leave ports open or expose sensitive data to the public internet.
- Injection attacks (SQL, LDAP, etc.): Attackers can exploit poorly written code to inject malicious commands into the backend systems.
- Cross-Site Scripting (XSS): XSS vulnerabilities allow attackers to inject malicious scripts into web pages viewed by other users, enabling them to steal cookies or session tokens.
By simulating an attack using these and other techniques, penetration testers help organizations patch vulnerabilities before they are exploited by hackers.
Penetration Testing vs. Other Security Tests
Many people confuse penetration testing with other types of security testing. Here’s a breakdown of how penetration testing compares to other common security assessments:
| Security Test | Description | Focus |
|---|---|---|
| Penetration Testing | Simulates a real attack to find and exploit vulnerabilities. | Finding and exploiting flaws. |
| Vulnerability Scanning | Automated process that identifies known vulnerabilities based on a database of issues. | Identifying known weaknesses. |
| Security Audits | A comprehensive review of security policies, processes, and practices. | Reviewing overall security. |
| Risk Assessment | A structured approach to identifying and evaluating risks to critical assets. | Evaluating potential threats. |
While vulnerability scanning is often an initial step in identifying weaknesses, penetration testing goes a step further by actively exploiting those vulnerabilities to assess the real-world impact. Security audits and risk assessments are also critical for understanding an organization’s security landscape, but they do not simulate attacks in the same way penetration testing does.

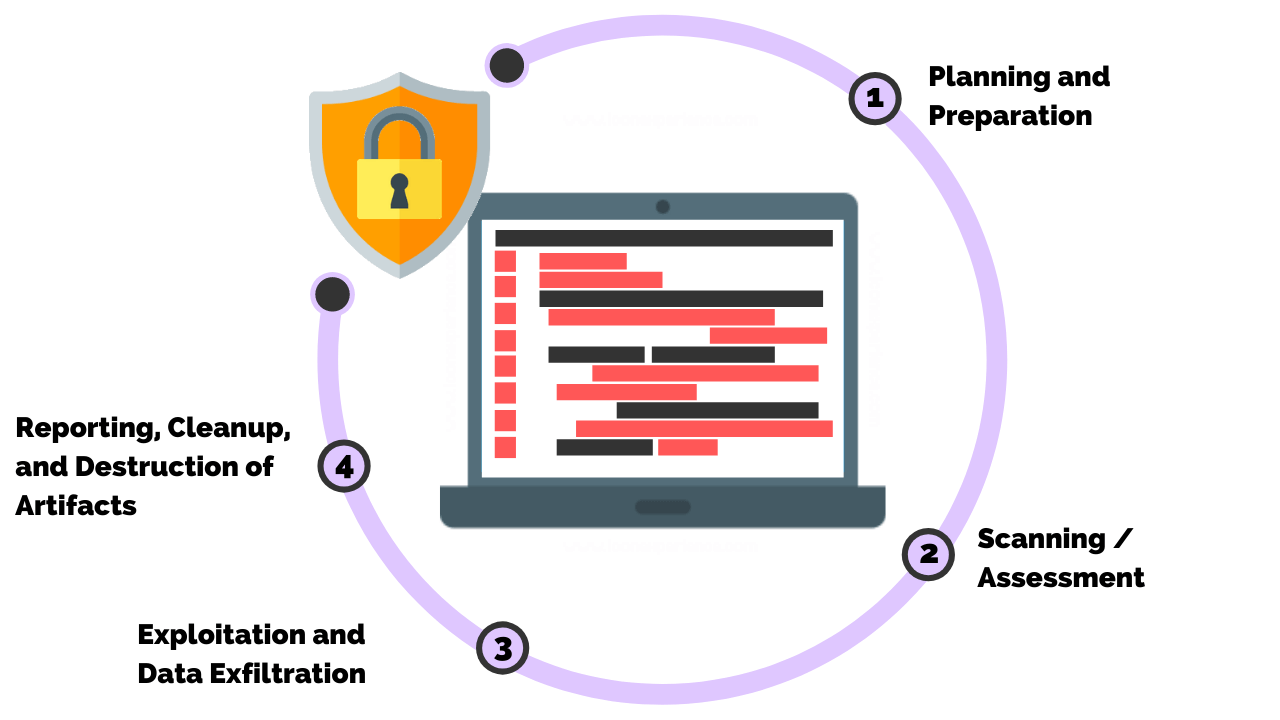
The Penetration Testing Process: How Is Penetration Testing Done?
Now that we’ve established what penetration testing is and why it’s essential, let’s dive into the pen testing process itself. Understanding how penetration testing is done involves a systematic approach that cybersecurity professionals follow to identify, exploit, and report on vulnerabilities. The process is typically broken down into several key phases, each crucial to ensuring thorough testing and effective results.
Step 1: Planning and Scoping
Planning and scoping are vital to the success of any penetration test. This phase is where both the client and the penetration testing team define the scope and objectives of the test, set boundaries, and establish rules of engagement. Here’s how it’s done:
Key Elements of Planning and Scoping:
- Understanding the Scope: The first step is to decide which systems, networks, or applications will be tested. It could include internal systems, external servers, web applications, databases, or mobile apps. The client needs to be clear about what areas they want tested to ensure the effort aligns with their security needs.
- Defining Rules of Engagement: This refers to the guidelines for how the penetration test will be conducted. It includes:
- Time limits: When the testing will occur to minimize disruption.
- Testing hours: Some organizations require testing to occur during off-peak hours.
- Communication: How the tester will report findings during the test and to whom.
- Boundaries: What systems and data are off-limits.
- Setting Objectives: It’s crucial to define the test’s objectives—what the penetration tester aims to discover, such as finding exploitable vulnerabilities, gaining unauthorized access, or assessing the overall security posture.
- White-box, Black-box, or Gray-box Testing: Based on the client’s needs, the testing team may perform white-box, black-box, or gray-box testing:
- White-box: Testers have full knowledge of the internal network, systems, and code.
- Black-box: Testers have no prior knowledge of the target systems and approach the test like real-world attackers.
- Gray-box: Testers have partial knowledge of the system (e.g., some internal documentation but no direct access).
Legal Considerations: One of the most critical aspects of planning is ensuring legal consent. Penetration testing must be authorized in writing, as unauthorized testing can lead to legal consequences. This agreement often includes non-disclosure agreements (NDAs), defining the scope, and clarifying liabilities.
Step 2: Information Gathering (Reconnaissance)
Once the planning phase is complete, the penetration testing team moves into information gathering or reconnaissance. This phase is essential for mapping the target and discovering potential attack surfaces. The goal is to collect as much data as possible about the target without triggering alarms.
Types of Reconnaissance:
- Passive Reconnaissance: In passive reconnaissance, testers gather information without directly interacting with the target system. This could involve:
- WHOIS searches: Finding domain registration details and IP address information.
- DNS queries: Identifying domain names, subdomains, and IP addresses associated with the organization.
- Public data sources: Searching for leaked data or documentation on social media, forums, or public repositories.
- Google Dorking: Using advanced search techniques to find sensitive information exposed online.
Passive reconnaissance helps the tester avoid detection while gathering valuable data.
- Active Reconnaissance: Unlike passive methods, active reconnaissance involves direct interaction with the target system to collect detailed information. This could include:
- Port Scanning: Tools like Nmap are used to identify open ports, services, and potential vulnerabilities on the target system.
- Service Fingerprinting: Identifying which versions of services (e.g., Apache, SSH) are running, which helps in finding known vulnerabilities in those services.
- Network Mapping: Tools like Traceroute and Netcat help identify the structure of the network, including devices and services.
Tools commonly used during reconnaissance include Nmap, Shodan, Maltego, and Recon-ng. Testers may also perform vulnerability scans to get an overview of known weaknesses.
Step 3: Vulnerability Assessment
In the vulnerability assessment phase, testers analyze the information gathered to identify potential weaknesses that could be exploited. This phase involves scanning, testing, and validating vulnerabilities.
Key Activities in Vulnerability Assessment:
- Automated Vulnerability Scanning: Tools like Nessus, OpenVAS, or Qualys scan the target systems to identify common vulnerabilities such as outdated software, unpatched systems, misconfigurations, and open ports.
- Manual Testing: While automated tools are useful, they cannot detect all vulnerabilities. Manual testing is required to discover complex vulnerabilities that tools may miss. Testers will use their knowledge to manually probe the system for weaknesses such as weak passwords, configuration flaws, and logical vulnerabilities.
- Prioritizing Vulnerabilities: Not all vulnerabilities are created equal. After scanning and manual testing, vulnerabilities are prioritized based on their severity and potential impact. High-risk vulnerabilities are often addressed first.
Common types of vulnerabilities that are identified during this phase include:
- SQL Injection: An attack that allows an attacker to execute arbitrary SQL code on a database.
- Cross-Site Scripting (XSS): Injecting malicious scripts into websites viewed by others.
- Broken Authentication: Weak or poorly implemented authentication mechanisms.
- Misconfigured Security Settings: For example, default credentials or improperly configured permissions.
Step 4: Exploitation
Exploitation is the phase where testers attempt to exploit the vulnerabilities they identified in the previous steps. This phase is critical to demonstrating how an attacker could gain unauthorized access or escalate their privileges within the system.
Key Activities in Exploitation:
- Exploiting Vulnerabilities: Penetration testers attempt to take advantage of identified vulnerabilities. This could be done by:
- SQL Injection: Gaining access to the database.
- Privilege Escalation: Using a low-level account to gain higher-level access (e.g., root or admin privileges).
- Buffer Overflow Attacks: Overwriting the memory of an application to execute arbitrary code.
Common tools used in this phase include Metasploit, Canvas, and Core Impact. These tools provide exploit modules that automate the exploitation of known vulnerabilities.
- Simulating a Real-World Attack: The goal is not just to find vulnerabilities but also to demonstrate how an attacker could use those vulnerabilities to breach systems, steal data, or cause harm.
Risk Considerations:
While exploiting vulnerabilities can provide valuable insights into the impact of a real attack, it also poses risks. Testers must take care not to damage the system, cause disruptions, or trigger false alarms. This is why thorough planning and communication with the client are essential.
Step 5: Post-Exploitation
Once the tester has successfully exploited a vulnerability, the post-exploitation phase begins. In this phase, the tester looks to explore the extent of the compromise and see how far they can move within the system.
Key Activities in Post-Exploitation:
- Maintaining Access: After gaining access, testers may attempt to maintain persistence within the system. This could involve installing backdoors or setting up secondary access points.
- Lateral Movement: Penetration testers move from one system to another within the network. This simulates an attacker who has gained access to one system and is attempting to compromise others.
- Data Exfiltration: The tester may simulate stealing sensitive data, like customer records or intellectual property, to understand the impact of a data breach.
- Escalating Privileges: Testers attempt to elevate their access rights to gain control of more critical systems and data.
The goal of post-exploitation is to mimic what a malicious actor would do if they were able to maintain access to the organization’s systems for an extended period.
Step 6: Reporting
The final phase of penetration testing is reporting. After completing the testing, the penetration testing team creates a detailed report that summarizes the findings, explains how vulnerabilities were exploited, and provides recommendations for remediation.
Key Elements of a Penetration Testing Report:
- Executive Summary: This section provides a high-level overview of the test, its goals, and key findings. It is designed for non-technical stakeholders like executives or business owners.
- Technical Details: This section includes the specifics of the test, such as the vulnerabilities discovered, the exploitation methods used, and any sensitive data accessed.
- Remediation Recommendations: The most critical part of the report is the remediation section, where testers provide actionable advice on how to fix the identified vulnerabilities. This could include software patches, configuration changes, or process improvements.
- Risk Assessment: The report also includes an assessment of the risks associated with each vulnerability, helping the client prioritize which issues to address first.
Penetration testing reports play a crucial role in improving an organization’s overall security posture.
Tools Used in Penetration Testing
To conduct a thorough and effective penetration test, cybersecurity professionals rely on various penetration testing tools. These tools aid in discovering vulnerabilities, exploiting them, and validating the security posture of a target system. Depending on the phase of the penetration test, different tools are used for tasks such as reconnaissance, vulnerability scanning, exploitation, and post-exploitation.
Popular Penetration Testing Tools
1. Kali Linux
Kali Linux is the de facto operating system for penetration testers. It’s a Debian-based Linux distribution that comes preloaded with a wide range of penetration testing tools. Kali includes everything a tester needs—from tools for information gathering, vulnerability analysis, and exploitation, to post-exploitation and reporting.
Some of the most popular tools in Kali Linux include:
- Nmap: A network scanning tool used for discovering hosts and services on a computer network.
- Metasploit: A framework for developing and executing exploit code against a target machine.
- Burp Suite: A comprehensive suite of tools for web application security testing.
Kali Linux’s ease of use, comprehensive toolset, and strong community support make it an essential tool for penetration testers.
2. Metasploit Framework
Metasploit is one of the most widely used tools in penetration testing, particularly for exploitation. This framework allows testers to develop and execute exploits against remote targets. It comes with a collection of exploit modules that automate the process of exploiting known vulnerabilities, but it also offers a command-line interface for developing custom exploits.
Metasploit also includes tools for payload generation, post-exploitation, and social engineering attacks, making it an all-encompassing framework for penetration testing.
Key Features of Metasploit:
- Automated Exploits: Quickly identify and exploit vulnerabilities in target systems.
- Exploit Development: Allows users to develop custom exploits for zero-day vulnerabilities.
- Meterpreter: A powerful post-exploitation tool that provides a command-and-control interface for compromised systems.
3. Burp Suite
Burp Suite is a web application security testing tool. It’s widely used for identifying security flaws in websites and web applications. The suite contains several powerful tools, including:
- Burp Scanner: Automated scanning for vulnerabilities like SQL injection, cross-site scripting (XSS), and more.
- Burp Proxy: Allows testers to intercept and modify web traffic between the client (browser) and the server.
- Intruder: A tool for automating brute-force attacks, such as cracking login credentials or attempting to guess hidden files.
Burp Suite is essential for testing web applications, especially in the context of common OWASP vulnerabilities.
4. Wireshark
Wireshark is an open-source network protocol analyzer that allows penetration testers to capture and analyze packets on a network. It is often used in reconnaissance and post-exploitation phases to understand network traffic and identify data that could be compromised.
Wireshark helps testers:
- Sniff traffic: Capture network packets to analyze protocols and communication between systems.
- Monitor for sensitive data: Look for unencrypted passwords, tokens, or other sensitive information passing over the network.
- Perform packet analysis: Identify network weaknesses and opportunities for further exploitation.
5. Nmap
Nmap (Network Mapper) is a widely used network discovery and vulnerability scanning tool. It helps penetration testers identify active devices on a network, open ports, and services running on those ports. Nmap is also capable of identifying operating systems, detecting vulnerabilities, and even running scripts to gather more detailed information.
Nmap is used during the reconnaissance and vulnerability assessment phases to map out the network and identify attack surfaces. Common use cases include:
- Port scanning: Identifying open ports that could be exploited.
- Service enumeration: Discovering which services are running on specific ports.
- OS detection: Identifying the operating system of a target machine.
6. Nessus
Nessus is a vulnerability scanner that automates the process of identifying vulnerabilities within an organization’s systems. It scans for known vulnerabilities, misconfigurations, and weak security policies across servers, routers, and other infrastructure components.
Nessus is most useful during the vulnerability assessment phase of penetration testing. Some of its key features include:
- Comprehensive vulnerability database: Nessus has an extensive vulnerability database that is regularly updated to cover the latest threats.
- Compliance checks: Nessus can be used to check systems for compliance with security policies and industry standards.
- Reporting: Nessus generates detailed vulnerability reports, which can help prioritize remediation efforts.
7. Aircrack-ng
For wireless network penetration testing, Aircrack-ng is a leading tool. It is used for monitoring and attacking Wi-Fi networks, and it includes capabilities like:
- Packet capture: Capturing packets to analyze the security of wireless networks.
- Cracking WEP/WPA keys: Breaking weak wireless encryption protocols (e.g., WEP and WPA).
- Network discovery: Identifying active wireless networks and their security protocols.
Aircrack-ng is critical for assessing the security of wireless networks, which are often the weakest link in many organizations’ infrastructures.
8. John the Ripper
John the Ripper is a password cracking tool that helps penetration testers assess the strength of password security. It uses various techniques, such as brute force and dictionary attacks, to crack password hashes.
John the Ripper is widely used to assess the robustness of passwords during the exploitation phase. It supports a wide range of hash types, including Unix-based password hashes, MD5, and Windows LM hashes.
Automated vs. Manual Penetration Testing Tools
While automated tools like Nessus or Nmap are great for quickly identifying known vulnerabilities, they are not a substitute for manual testing. Automated tools can miss complex or subtle vulnerabilities, which is why penetration testers also rely on their expertise and manual methods.
Advantages of Automated Tools:
- Speed: They can scan large networks or applications quickly and identify common vulnerabilities.
- Accuracy: Automated tools are highly effective in identifying known vulnerabilities based on well-defined signature databases.
Advantages of Manual Testing:
- Complexity: Manual testing is essential for finding advanced or zero-day vulnerabilities that automated tools might miss.
- Customization: Testers can customize manual attacks based on the specific architecture or needs of the organization.
Best Practice: A combination of both automated and manual testing provides the best coverage for a penetration test. Automated tools can perform the heavy lifting, while manual testing uncovers sophisticated vulnerabilities.

Penetration Testing Methodologies
In the world of penetration testing, following a structured and standardized approach is critical for ensuring that tests are thorough, repeatable, and effective. This is where penetration testing methodologies come into play. These methodologies provide penetration testers with frameworks for conducting systematic tests, helping them identify vulnerabilities in a consistent and organized manner.
Industry-Standard Methodologies for Penetration Testing
1. OWASP Testing Guide
The OWASP (Open Web Application Security Project) Testing Guide is a comprehensive resource for testing the security of web applications. It is widely regarded as a foundational methodology for web application penetration testing.
The OWASP Testing Guide includes detailed testing procedures for the following areas:
- Authentication: Testing the security of login mechanisms.
- Session Management: Ensuring that session tokens are secure and cannot be hijacked.
- Access Control: Checking for unauthorized access to sensitive resources.
- Input Validation: Identifying vulnerabilities like SQL injection, Cross-Site Scripting (XSS), and Cross-Site Request Forgery (CSRF).
- Error Handling: Ensuring that applications don’t expose sensitive information through error messages.
The guide is continuously updated to reflect the latest web application vulnerabilities and is a go-to resource for penetration testers performing security assessments on web apps.
2. PTES (Penetration Testing Execution Standard)
The Penetration Testing Execution Standard (PTES) provides a detailed methodology for performing penetration tests, covering everything from the initial scoping phase to the final reporting. PTES is unique in its focus on providing a structured and repeatable process for penetration testing.
PTES breaks the testing process into several key stages:
- Pre-engagement Interactions: Initial planning, scoping, and agreement on rules of engagement.
- Information Gathering: The reconnaissance phase, where data is collected about the target.
- Threat Modeling: Identifying potential attack vectors and modeling threats based on the target’s architecture.
- Vulnerability Analysis: Identifying weaknesses and potential points of exploitation.
- Exploitation: Attempting to exploit identified vulnerabilities.
- Post-Exploitation: Gaining deeper access into the system to demonstrate the impact of the vulnerabilities.
- Reporting: Documenting findings and providing remediation recommendations.
The PTES methodology is flexible, meaning it can be adapted to suit various penetration testing scenarios, such as testing networks, web applications, or systems.
3. OSCP (Offensive Security Certified Professional)
The Offensive Security Certified Professional (OSCP) is one of the most respected certifications in the cybersecurity industry. OSCP follows a hands-on approach to penetration testing and promotes a methodology that emphasizes creativity and persistence.
The OSCP methodology includes:
- Reconnaissance: Gathering information about the target system using various open-source tools and techniques.
- Vulnerability Analysis: Identifying potential weaknesses in the target system.
- Exploitation: Attempting to exploit vulnerabilities to gain access to the system.
- Post-Exploitation: Gaining deeper access into the system and escalating privileges.
- Reporting: Writing up findings, including both technical details and suggested remediation strategies.
The OSCP methodology stresses the importance of creativity and persistence, as real-world attacks often involve overcoming obstacles and thinking outside the box.
4. NIST SP 800-115
The National Institute of Standards and Technology (NIST) Special Publication 800-115 provides guidelines for conducting penetration tests on federal systems. NIST’s approach is particularly valuable for organizations that need to adhere to regulatory frameworks, such as those in government or industries handling sensitive data.
NIST 800-115 covers the following phases:
- Planning: Identifying objectives, scoping, and agreeing on testing rules.
- Discovery: Identifying network and system architecture, scanning for open ports and services.
- Exploitation: Attempting to compromise systems to demonstrate the impact of vulnerabilities.
- Post-Exploitation: Documenting successful exploitation and determining how far the attacker could have gone in terms of lateral movement and privilege escalation.
- Reporting: Delivering clear, actionable reports to the client.
This methodology is highly structured, making it ideal for organizations that need to follow a strict, compliance-driven approach to penetration testing.
White-box vs. Black-box vs. Gray-box Testing
One of the most important decisions in the penetration testing process is determining the level of access the tester will have to the target system before starting the test. This is where the concepts of white-box, black-box, and gray-box testing come into play.
1. White-box Testing
White-box testing (also known as clear-box or open-box testing) is when the penetration tester has full access to the target system. This could include:
- Source code of applications.
- Network diagrams.
- Internal configuration files.
- Access to credentials and user permissions.
The purpose of white-box testing is to simulate an insider threat or assess the security of a system with full knowledge. This approach allows the tester to:
- Review the code for security vulnerabilities.
- Test the system for design flaws.
- Identify internal access control issues.
White-box testing is often more thorough and efficient, as it gives the tester all the information they need upfront.
2. Black-box Testing
In black-box testing, the tester has no prior knowledge of the system being tested. The tester approaches the test as an external attacker would, using only external information (e.g., publicly available data, reconnaissance, and vulnerability scanning) to discover and exploit weaknesses.
Black-box testing simulates real-world attack scenarios where hackers have no inside knowledge of the target and rely on reconnaissance and exploitation techniques to identify vulnerabilities.
3. Gray-box Testing
Gray-box testing is a hybrid approach, where the tester has partial knowledge of the system. This might include access to some internal documentation or limited access to credentials. The idea behind gray-box testing is to simulate an attack from an insider with moderate access, such as a user with low-level access trying to escalate privileges.
Gray-box testing provides a balance between the comprehensive scope of white-box testing and the realistic scenario of black-box testing.
Penetration Testing Methodology Best Practices
Regardless of the specific methodology you choose, there are certain best practices that should always be followed to ensure a thorough, effective, and ethical penetration test:
- Clear Scoping: Always define the scope of the penetration test upfront to avoid testing areas that are off-limits or causing disruption to normal business operations.
- Regular Communication: Maintain communication with the client throughout the process, especially in case an urgent vulnerability is discovered.
- Test All Layers: Ensure that every part of the system is tested, including the network, applications, endpoints, and even the human factor through social engineering attacks.
- Minimize Disruption: Penetration tests should be conducted in such a way that they do not disrupt normal business operations or damage critical infrastructure.
- Post-Test Remediation: Provide actionable and detailed recommendations on how to fix the identified vulnerabilities, helping the client address issues effectively.